EscapeTwo

Enum
nmap
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
ldap
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
nxc
rid-brute
rid-brute的原理参考mane大佬写的吧https://manesec.github.io/2023/10/28/2023/2023-10-rid-brute/
我在这里摘录一些mane的话,也许我可能在下一周内从数据包的角度来看一看sid爆破呢?
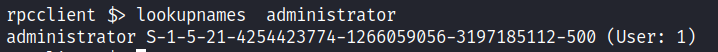
在 Windows 也是如此,新建的用户 rid 也是从 1000 开始,为了不和 build in 用户重合,build in 用户会从 500 开始,一些 buildin 组也会有 rid(比如:512代表只读域控制器)administrator 的 rid 通常是 500。
为了解决在多个 DC 中不同子域的 RID 重合问题,Windows 默认会给每个 DC 安排一个 domain sid,然后把 DC 下的用户合成新的 SID,以识别用户来自哪里。
例如:
当 domain 的 sid 为
4254423774-1266059056-3197185112默认的 users 通常以
S-1-5-21开头 ,合起就是
S-1-5-21-4254423774-1266059056-3197185112因为 administrator 的 rid 是 500,在后面加上 500 就变成了
S-1-5-21-4254423774-1266059056-3197185112-500
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
整理一下内容得到可能的用户名,然后执行一下密码喷洒。
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
没有一个成功的,很气。转头看一眼smb服务
smb
通过凭据登录进去找到了两个文件
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
拿出来打开看看
hex edit fix file head
直接打开发现文件头损坏读不出来拿到winhex里面修改成正确的文件头
accounting_2024.xlsx
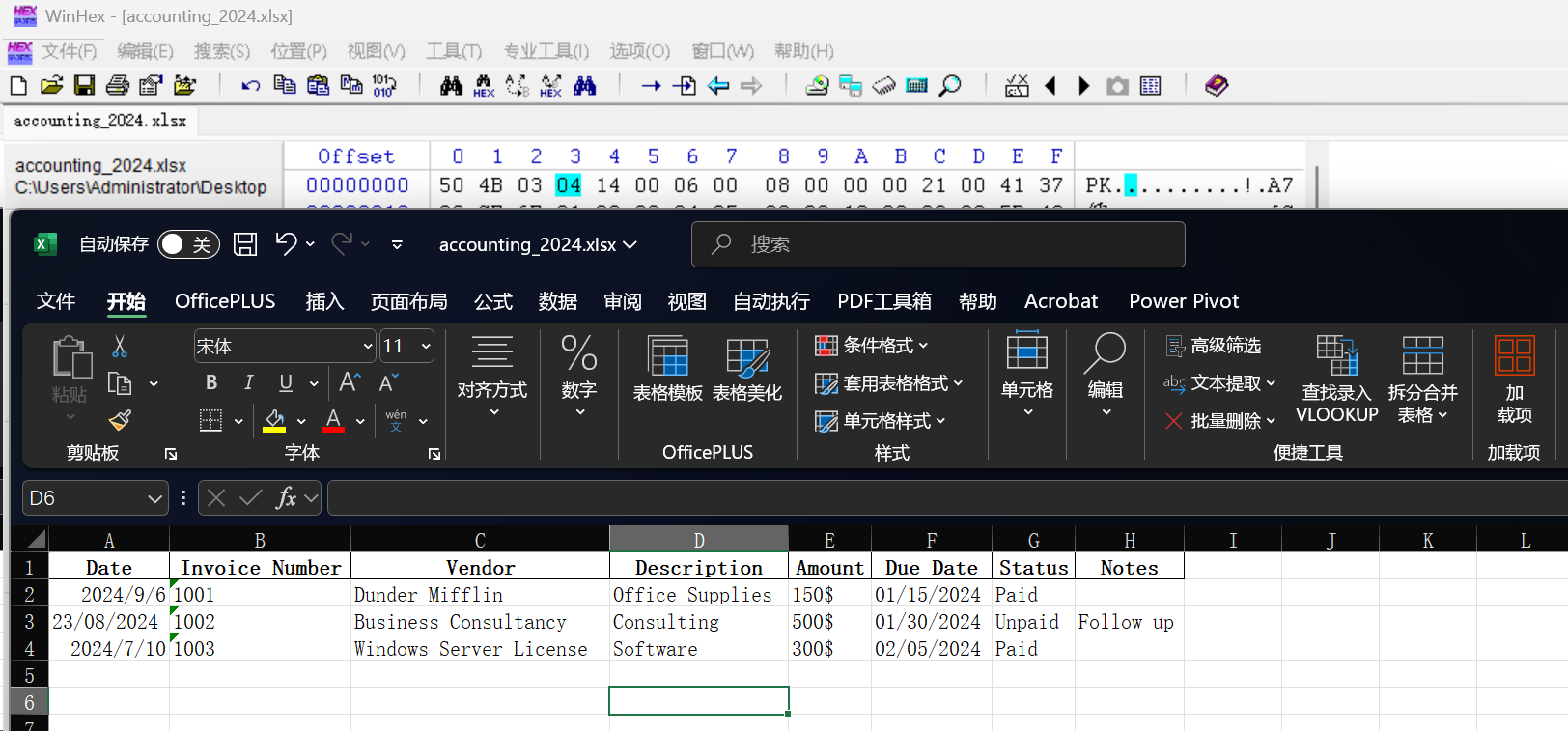
accounts.xlsx
| First Name | Last Name | Username | Password | |
|---|---|---|---|---|
| Angela | Martin | angela@sequel.htb | angela | 0fwz7Q4mSpurIt99 |
| Oscar | Martinez | oscar@sequel.htb | oscar | 86LxLBMgEWaKUnBG |
| Kevin | Malone | kevin@sequel.htb | kevin | Md9Wlq1E5bZnVDVo |
| NULL | NULL | sa@sequel.htb | sa | MSSQLP@ssw0rd! |
得到了一些账号和密码,继续提取可能的username和password做一下密码碰撞。
nxc
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
得到了用户sequel.htb\oscar:86LxLBMgEWaKUnBG重新看一眼smb以及看看是否有wrm权限。结果都没有什么发现
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
可以注意到之前有一个我们很感兴趣的用户名和密码 sa:MSSQLP@ssw0rd!用nxc看一下是否能够登录
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
成功登录,那么我们反弹一个shell出来。
1 | PS C:\Windows\system32> whoami |
翻翻找找又能翻到一个密码
1 | PS C:\sql2019\ExpressAdv_ENU> type AUTORUN.INF |
把它加到我的小本本里面继续狠狠喷洒密码
Own User
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
evil-winrm登录
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
传个狗上去看看域关系
1 | ┌──(kali㉿kali)-[~/HTB/Escapetwo] |
ok剩下的就不会了,又是看不懂域渗透的一集。菜就多练,我直接回去多练。等我学会狗图怎么看了我再回来!
从mane的blog学到了weevely这个shell管理器,看着好方便的样子,明天学学去。┗|`O′|┛ 嗷~~,好像已经到明天了的样子qaq。睡觉!
mane的blog好像是自己写的呢,我也想要有自己的写的blog
- Title: EscapeTwo
- Author: EnchanterW
- Created at : 2025-05-10 09:00:00
- Updated at : 2025-09-20 20:06:49
- Link: https://enchanter-w.github.io/2025/05/10/EscapeTwo/
- License: This work is licensed under CC BY-NC-SA 4.0.